The most common cyber attacks in 2025 include ransomware, phishing, malware, spear-phishing, whale-phishing, denial-of-service (DoS), man-in-the-middle (MITM), zero-day exploits, brute force attacks, and SQL injections. These threats are increasing in Australia, with SMBs making up nearly half of all targets. Businesses can protect themselves with patching, backup and recovery, staff training, and the Australian Cyber Security Centre’s Essential Eight strategies.
A cyber attack is any form of intentional and malicious digital intrusion or breach into an organisation’s software, systems, servers, networks or websites. Another entity, be it an individual hacker, an organisation, or even a state actor, perpetrates the attack, attempting to gain access to, damage, or destroy some element of the target organisation’s digital estate.
These two terms are not interchangeable: a cyber threat is a potential attack, one that hasn’t launched against your business. A cyber attack is an actual or attempted targeting.
While the 10 most common cyber attack methods remain a significant threat, 2025 has introduced new variations and evolving tactics that businesses need to prepare for. Cyber criminals are using AI, automation, and supply chain vulnerabilities to expand the attack surface and exploit weak security measures.
Here are some of the most important cybersecurity threats in 2025 that go beyond the traditional methods:
These new forms of cybersecurity attacks don’t replace the traditional threats like malware, brute force, or SQL injection attacks — they amplify them. The result is a more complex cyber risk environment, where inadequate security measures can quickly lead to data breaches, financial losses, and significant downtime.
Australian organisations can’t afford to treat these as hypothetical risks. Attackers gain access faster, exploit technical vulnerabilities more effectively, and cause more severe business disruption than ever before.
Working with a trusted cyber security expert such as Canon Business Services ANZ (CBS) gives you access to automated tools, advanced security systems, and 24/7 monitoring to defend against both established cyber attacks and these new 2025 threats.
Cyber attackers are a creative bunch, and the list of ways they can hurt businesses is a lengthy one. Here are just a few examples:
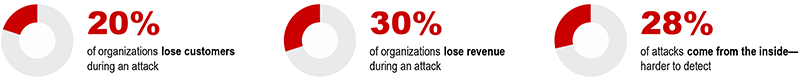
• Cyber attacks can cause operational disruptions by taking systems offline.
• They can destroy customer trust through a data breach involving customers’ private information.
• In regulated industries, certain breaches can create regulatory compliance nightmares, too.
• Ransomware attacks can render systems inoperable and cost businesses in the millions should they choose to pay.
In general, a cyber attack works because attackers gain access to or control of some element on the target business’s network. Once attackers gain access, they can execute any number of malicious actions, from stealing data to locking systems in demand of payment to disabling and damaging systems.
Transform Your Cyber Defense: Prioritised Actions for Staying Ahead of Threats.
DownloadThe specific methods and outcomes of cyber attacks can vary widely. Most attacks and threats fall into the following 10 categories.
A broad term that includes numerous kinds of malicious software. Malware finds a way into your company’s network or connected systems, often from a user clicking a malicious link or opening a malicious attachment. Once active, malware can execute a number of attacks, such as logging and stealing data in a data breach (spyware) or causing the system to fail entirely.
An especially dangerous and problematic subset of malware, ransomware attacks lock a business (or even a government agency or piece of critical infrastructure) out of infected systems and demand payment to regain access. Attackers may threaten to leak or sell confidential data if not paid. Businesses may be unable to function normally until systems are restored. Disaster recovery procedures are one way to combat this threat: if systems are properly backed up (prior to infection), they can usually be restored.
Phishing attacks originate over communications, usually email. Phishing emails mimic an important, reputable sender (perhaps even a vendor a business is using, such as Microsoft 365) and push readers to click a link and provide sensitive information (login credentials, for example). The site is a fake and the data goes to the attacker, putting IT security at risk. Phishing attacks are common in both consumer and business contexts. Either way, the attackers are looking to steal personal information and gain account access.
Spear-phishing is highly targeted phishing: instead of sending an email to millions pretending to be Apple or a large bank, spear-phishing attackers research specific targets within specific organisations and then use social engineering to deceive their way in. They may pretend to be a high-ranking executive asking via urgent email for employees (sometimes by name!) to do something unusual and unsafe. The best attacks are indistinguishable to the average user, but they are also hard to execute successfully.
Almost the reverse of spear-phishing, whale-phishing attacks target those executives directly. Attackers may use targeted ransomware to steal or lock sensitive data or proprietary information.
Denial of service (DoS) attacks send high volumes of (fake) traffic to a server or other system, eating up all available bandwidth and choking out legitimate traffic. Malware installed across numerous machines can perpetuate this at scale, called a distributed denial of service attack (DDoS attack).
An attacker who jumps in between what should be secure traffic between two parties is executing a man-in-the-middle attack. This threat can steal data from a transaction—and neither legitimate party will know. These attacks occur after malware is installed or when users operate on insecure networks (like public Wi-Fi).
Software providers regularly discover—and patch out—vulnerabilities within their software. Sometimes an exploit becomes well-known, but the developer needs time to produce a fix. Zero-day exploits attack these known vulnerabilities prior to the patch. A related vulnerability is unpatched, out-of-date systems. Zero-day exploits are difficult to catch but rare. Breaking an old, unpatched system that’s widely known to be vulnerable is much easier.
What most people think of when they hear the word “hack”: a brute force attack breaks into a system via sheer strength, whether by using bots and tools to guess password combinations at superhuman speeds. Vulnerability management tools can mitigate simple brute force attacks by limiting the number of login attempts before lock out.
SQL injection attacks work by injecting malicious code into an SQL database, usually for the purpose of stealing information contained in the database. SQL injection attacks can be executed using a text input field on a public-facing website, making them particularly worrisome.
Understanding the dangers involved and the methods by which you may be attacked is a starting point, but implementing effective strategies to combat cyber threats is the true goal.
If you haven’t given much consideration to cyber security as an organisation, the first step is to take care of common-sense security vulnerabilities and gaps. Keeping software and firmware up to date across all systems takes effort, but it doesn’t require deep IT knowledge.
Even if you’re not working with a managed IT security partner, there are basic business-oriented steps you can take right away. As a place to start, the Australian government has assembled some initial tools to help you protect your business.
Once you have those basics in place, the ASCS provides additional key guidance called the Essential Eight. These eight cyber threat mitigation strategies are a great next step in protecting your business.
Most organisations need to go deeper, though, which likely involves a managed IT partner that can modernise and keep current your business’s digital defences.
For example, setting up backup and disaster recovery solutions across your enterprise requires a bit more investment and technical know-how than many businesses have on hand. The same is true of setting up governance procedures, training your staff in cyber best practices, and many other elements of your cyber security defence strategy. The same is true of setting up governance procedures, training your staff in cyber best practices, even having a SOC as a service, and many other elements of your cyber security defence strategy.
Canon Business Services ANZ (CBS) is a full-service IT partner serving organisations of all sizes, specialising in enterprise businesses. We offer a comprehensive range of security services as a secure MSP, though also a provider of Managed Security Services, and additionally a 24/7 Security Operations Centre (SOC).
Canon Business Services ANZ (CBS) offers comprehensive, cutting-edge cyber IT security protection, including vulnerability management, Security Information and Event Management systems (SIEM), and firewall management systems.
Don’t gamble with the threat of the different types of cyber attacks and the damage they can do to your business, your systems, and your reputation. Step into an active, cyber-secure future with CBS instead.
Ready to access industry-leading cyber security protection? Reach out to our team today.
The most common cyber security threats today include phishing attacks, ransomware attacks, malware attacks, denial of service (DoS) and DDoS attacks, SQL injection attacks, and insider threats. These cyber attacks target critical systems, sensitive data, financial information, and user accounts, often exploiting weak security measures or human error. If attackers gain access, they can steal data, cause significant downtime, disrupt operations, and lead to financial and reputational damage.
A data breach happens when attackers gain unauthorised access to a computer system or network, often through phishing emails, malicious websites, or injecting malicious code. Once inside, they can steal sensitive data such as login credentials, financial data, or personal details. This type of cybersecurity attack can cause operational disruption, financial losses, lost revenue, and legal consequences, especially if critical data or confidential information is compromised.
A cyber threat is a potential risk that could exploit a vulnerability in your systems, while a cyber attack is when attackers gain access and actively attempt to disrupt operations, steal data, or damage critical infrastructure. In short, cyber threats are potential threats, while cyber attacks are real events. Businesses must address both by applying security measures such as multi-factor authentication, antivirus software, security patches, and employee training.
An attack surface refers to all possible entry points where cybersecurity risks exist and attackers can gain unauthorised access to critical systems. This includes user accounts, endpoints, applications, cloud services, supply chain attacks, and even insider threats. A wide attack surface increases cyber risk, exposing businesses to data loss, significant downtime, or financial impact. Organisations can reduce such threats with security systems, automated tools, content delivery networks, complex passwords, and cybersecurity awareness training to mitigate risks.