Large or small, no organisation is immune to sophisticated and determined cyber-criminals. What’s an even more scary thought is that too many companies invest in only standard cyber security defences such as firewalls, antivirus software, and virtual private networks.
For example, the international Marriott hotel group suffered a string of massive data breaches that exposed more than 300 million guests. But what stunned professionals in the managed IT and cyber security sector was that hackers hid in plain sight for upwards of four years.
Had the hospitality corporation properly utilised a Security Information Event Management (SIEM) system, it would likely have detected hackers before any significant financial and reputational damage was done. If you are concerned about your business getting hacked, SIEM solutions may be right for you.
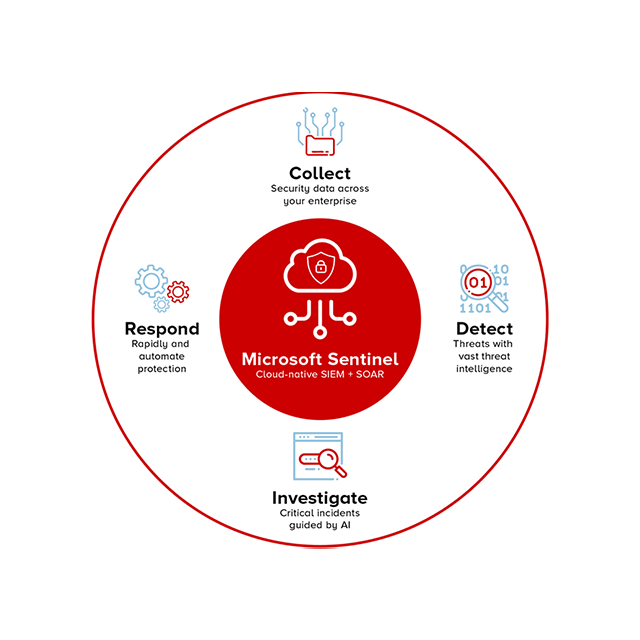
SIEM solutions are a natural next step that blends Security Information Management (SIM) and Security Event Management (SEM). The IT security strategy essentially gathers data from devices, physical servers, Cloud spaces, and endpoint devices, among others. It stores the information and evaluates it using next-generation analytics.
In doing so, suspicious trends, anomalies, and user behaviour trigger alerts. Cyber security specialists field the alerts and take proactive measures to isolate and eradicate threats. These are examples of how SIEM solutions can be applied.
• Track System Changes
• Detect Phishing Emails
• Identify Compromised User Credentials
• Flag Unusual Account Behaviour
• Centralise Log Management Data
Perhaps the most tangible benefit for business leaders involves deterring a cyber attack before network disruptions occur. This advanced form of cyber hygiene is well known for its threat hunting capabilities. In other words, security teams can flip the script on threat actors by playing offence.
If SIEM were as simple as downloading the latest antivirus software update and running a scan, every outfit would onboard it. But like any industry leading approach, it poses several challenges for businesses. These typically include the following.
• SIEM Requires a material Investment
• Cyber Security Specialists are Needed to Fine Tune SIEM
• Alert System May Not Provide Context
• SIEM Tools Require Maintenance
It’s important to understand these and other challenges can be deftly handled with the right managed IT security support. Addressing them allows organisations to move forward with improved governance, compliance, and data security.
Implementing a SIEM system identifies emerging threats and allows security professionals to respond in real time. This advanced approach to establishing a strong cyber security defence generally meets or exceeds the minimum monitoring requirements spelled out in government regulations.
It will be incumbent upon each unique business to communicate its compliance and governance needs to configure its SIEM solutions. But the fact that security systems can be enhanced with next-generation machine learning, behaviour identification, and algorithms makes it a boon for over-regulated industries.
Our internet-driven business culture has resulted in companies utilising wide-reaching devices and data storage options. The inherent lack of physical centralisation overburdens in-house security personnel. It’s not uncommon for companies to use multiple Cloud spaces and endpoint devices with access to their network. But what may be even more concerning is the growing remote workforce.
SIEM solutions allow a company’s security arm to bring all those moving parts under one umbrella. When a new hire logs into the network from another city, their activity goes under the microscope, just like an onsite employee accessing a local network connected desktop. Perhaps the key reason SIEM delivers a cyber security uplift is because everything is monitored, all the time.
Unlike a SIEM, a Security Operations Centre (SOC) is a team of specialists who analyse and address emerging threats. An SOC is typically established to provide 24/7 monitoring, largely because threat actors are just as likely to strike during the dead of night. The experienced and certified cyber security professionals who staff the SOC possess the skills to implement threat hunting strategies. A SOC team will utilise a SIEM as part of their role.
In many ways, SIEM and SOC are like two sides of a cyber security coin. SIEM solutions provide real-time monitoring and advanced vulnerability management. An SOC, in turn, brings human intelligence into the equation. The security experts in an SOC distinguish harmless anomalies from the criminal acts of hackers.
A Security Orchestration, Automation, and Response (SOAR) system automates SIEM-related processes to help fast-track incident response. The focus of SIEM is primarily on unusual user behaviour and log traffic, among others. A SOAR takes that SIEM information, analyses it, and reduces the number of routine tasks performed by SOC team members. A SOAR can also be configured to automatically respond to low-level threats without necessarily taking time away from security specialists. In essence, SOAR provides additional value to SIEM and SOC investments.
Transform Your Cyber Defense: Prioritised Actions for Staying Ahead of Threats.
DownloadThere are two factors that motivate companies to choose managed IT services over hiring a full-time team. The cost of hiring cyber security staff members strains budgets because they require ongoing training to stay abreast of new technologies and emerging threats. The second reason involves the growing cyber security labour shortage.
That’s why 37 per cent of small businesses reportedly outsource to a third party managed security services provider (MSSP). And upwards of 92 per cent of the Forbes Global 2000 companies also outsource. Truth be told, the cost of building an in-house SIEM often proves prohibitive, even if you can onboard enough cyber security specialists to provide 24/7 monitoring.
What is managed SIEM? Managed SIEM (Security Information and Event Management) refers to the practice of outsourcing the implementation, monitoring, and maintenance of SIEM solutions to a specialized service provider. This approach allows organizations to leverage the expertise of cybersecurity professionals and advanced tools, ensuring proactive threat detection, incident response, and compliance with industry regulations. Business professionals who prefer to keep everything in-house discover that outsourcing to a managed service provider comes with substantial benefits. Along with not taking on a distraction from goal-achieving practices, the managed SIEM can enhance their security posture and focus on core activities while leaving the intricacies of security management to experienced professionals.
On-Demand security expertiseAlthough SIEM remains an excellent tool, it cannot replace human decision-making. Coupling a SIEM with a Security Operations Centre [SOC] staffed by experts ensures proactive measures are taken to repel threat actors.
Third party managed IT security firms provide scalable monthly and annual agreements. This allows businesses to pay only for the managed IT security services they require. It’s also common for an MSSP to offer ongoing flexibility, so organisations can make changes on a need basis.
Industry leaders have good reason to worry about debilitating cyber-attacks. Creating a SIEM requires purchasing and leasing software and IT infrastructure. Once all the moving parts are acquired, it takes time for in-house IT staff to reconfigure aspects of the network and implement SIEM solutions. Along with being cost-prohibitive, going it alone takes a long time. By contrast, a third party IT security provider already has everything in place.
Unless your operation is involved in forward-looking technology, you can anticipate lagging behind the curve. Managed IT security firms are in the business of tracking the latest and most effective cyber security measures. This enables you to stay ahead of the latest tactics, techniques, and procedures (TTPs) hacking groups implement and ensure the fastest possible response.
Perhaps the greatest benefit industry leaders enjoy is knowing their business and livelihood are well protected. Not waiting or worrying about a late-night phone call indicating your business suffered a data breach or ransomware attack is priceless.
For any security approach to work, it must seamlessly tie into an operation’s best practices, goals, and potential for growth. SIEM solutions have experienced increased popularity because they deliver. If you are interested in integrating a SIEM, along with selecting the right MSSP partnerthese are checklist items to consider,
The wide-reaching devices, routers, firewalls, and servers create different log types. It’s essential to consult with a SIEM expert to develop a solution that is up to the task. However, an experienced managed IT security provider can usually configure log collectors for any log source to work with a SIEM.
The SIEM you select will likely include ready-made alert and reporting templates. It’s critical to customise and refine these and other elements for your business to maximise your alert and compliance benefits.
Choosing the best SIEM to serve your business needs calls for harmonious implementation. It needs to effectively work with existing cyber security measures and IT infrastructure.
The proactive nature of SIEM solutions separates them from reactionary models. The best SIEMs can provide threat context, recognise user behaviour shifts, and deliver actionable alerts in real time. This type of predictive intelligence helps security professionals target threats.
Canon Business Services (CBS) can help you get started or continue on your cyber security journey. Our team would initially start with a Cybersecurity assessment to establish a baseline and determine the best strategy moving forward, that combines quick wins along with establishing longer term cyber defences.
CBS provides scalable and effectively managed IT security for organisations across various industries, including Financial Services, Healthcare, Manufacturing and Government. If your company would benefit from our SIEM expertise, contact CBS for personalised support.
Canon Business Services ANZ (CBS) is one of Australia’s most highly accredited Cybersecurity services organisations. We’re proud to be among the few Australian MSSPs in the Microsoft Intelligent Security Association (MISA), which means we can better defend you against a world of increasing cyber threats. CBS is one of the few MSSP’s holding three Azure Advanced Security Specialisations, across Identity & Access Management, Cloud Security and Threat Protection. We know what's required to safeguard your organisation today.