The COVID-19 pandemic forced businesses to pivot at the drop of a hat, fuelling the already nascent rise of remote work—a trend that’s likely to persist long into the post-pandemic future. While the ability to work from anywhere has benefits for businesses and employees alike, it also necessitates a re-evaluation of cybersecurity strategy, which starts with conducting a cybersecurity assessment.
Last month was Cybersecurity Awareness Month, a collaborative effort between the government and the Australian Cybersecurity Center (ACSC) that functions as a reminder to all Australians to stay safe online. This year’s theme, “Have you been hacked?” further reinforces the need to enhance cybersecurity strategy across government bodies and corporate enterprises alike.
As cybersecurity expert Chuck Brooks reports, “Unfortunately, despite global efforts, every subsequent year the numbers get worse and show that we are far from being able to mitigate and contain the numerous cyber threats targeting both industry and government”.
An airtight cybersecurity strategy should be top of mind for every business leader right now. Increasing your knowledge of the IT security lifecycle and conducting a cybersecurity assessment are crucial steps to supporting risk management and data protection efforts across your entire organisation.
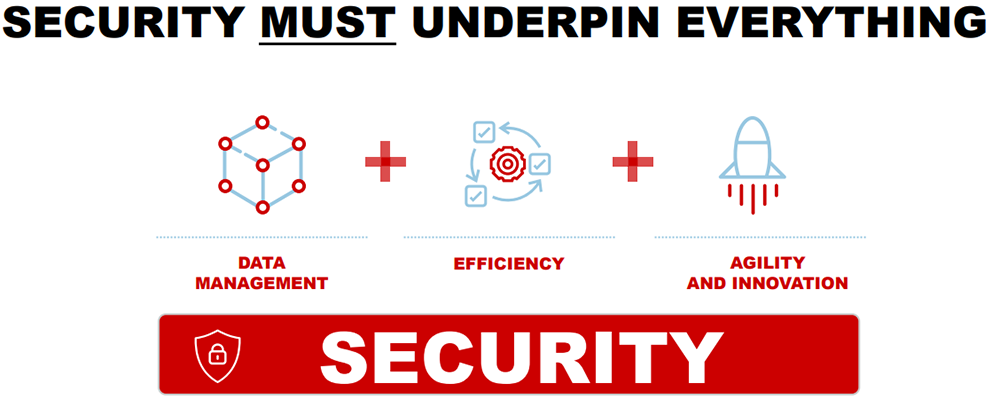
The IT security lifecycle is a series of actions that business leaders can take on an ongoing basis that helps to ensure the security of their most valuable assets.
There are four essential components of the security lifecycle:
1. Identify and deepen: Familiarise yourself with your assets—which include endpoint devices, data, and IP—and deepen your knowledge of your environment. You can’t protect what you can’t see, so you need to know where your most valuable assets live and who has access to them. This will ensure that your cybersecurity strategy is continuously improving and evolving in line with your business.
2. Assess: Determine the value and level of risk for each asset. You can’t protect everything, so prioritising your most valuable assets is key. The CIA method—Confidentiality, Integrity, Availability—provides the criteria by which you can identify and prioritise your assets.
3. Remediate and protect: Implement advanced security controls and test them to ensure they’re working properly.
4. Monitor and respond: Be proactive—monitor your network regularly to identify potential threats early on.
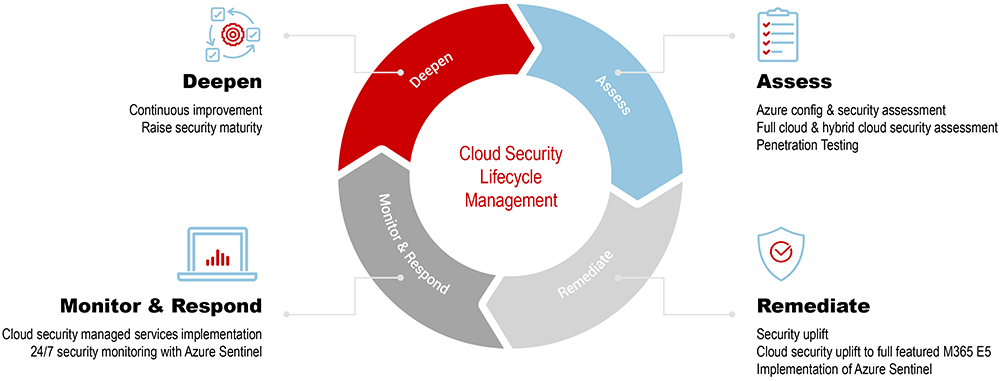
Implementing these steps will ensure you’re continually assessing and monitoring your environment to help safeguard against cybersecurity attacks as threats continue to increase in frequency and sophistication.
Transform Your Cyber Defense: Prioritised Actions for Staying Ahead of Threats.
DownloadWith increases in cloud adoption and hybrid work models, employees can—and do—work from virtually anywhere. This dramatically increases the “attack surface” of an organisation, meaning the number of possible entry points that could provide unauthorised access to your network.
Some international industry standards and government authorities aim to regulate cybersecurity by enforcing stricter cybersecurity compliance criteria to reduce financial loss and protect their reputation. In order to meet the standards set by certain regulating bodies, such as APRA or ISO, a security assessment is required.
Another factor to consider is the effect of current geopolitical events on the cybersecurity landscape. The recent Russian invasion of Ukraine forced hackers to take sides in the conflict, indicating a potential shift in how cyber groups will behave in the future. Prior to the invasion of Ukraine, Russian hackers targeted a list of Fortune 500 companies. The frequency of these cyber attacks has dramatically increased in response to Western support for Ukraine.
Similarly, the Australian government’s condemnation of Russia and support for Ukraine resulted in an increase in cybersecurity attacks against large corporations in Australia. At this point, it’s not a matter of if your organisation will experience a cyber threat, but when. The implications of failing to adopt a cybersecurity strategy have the potential to be disastrous, as evidenced by the recent attacks on Optus, Medibank, the Australian Defence Department, and the Australian Federal Police.
Conducting a cybersecurity assessment keeps you in control of your environment and mitigates all forms of cyber risk.
A cybersecurity assessment plays an important role in finding known and unknown vulnerabilities amongst your systems.
Think of it like a medical check-up. Getting regular check-ups with your doctor can help spot potential health issues before they become a problem. In the same way, conducting regular security assessments makes it possible to diagnose weaknesses in your network and take proactive action in order to save time and money in the future.
Conducting a security assessment also gives you a better understanding of your assets. Asking questions like these can help you to get a- better idea of what you’re working with, as well as reveal areas of opportunity to improve your security posture:
• How is your data stored?
• Where is your data stored? Is it on-premises, in the cloud, or do you use a hybrid model?
• Who has access to your data, internally and externally?
Two key assessments we perform often for our customers are ACSC Essential 8 and our Cloud Security assessment.
Remember, a cybersecurity assessment is not a one-and-done deal, but part of the ongoing maintenance of your IT security lifecycle. Annual cybersecurity assessments were once considered standard, but it is now recommended they be conducted quarterly.
As the cybersecurity landscape shifts, your business has the potential to be exposed to insidious new threats. Regular assessments help you account for your own blind spots and reduce the potential for human error.
The best way to conduct a cybersecurity assessment is to work with a third-party provider like Canon Business Services ANZ (CBS), who has the tools and knowledge to test your network and diagnose any potential vulnerabilities.
CBS can help you take stock of the current state of your network, identify areas for improvement, and provide you with a roadmap to secure your network and ensure you meet cybersecurity compliance criteria.
To learn more about how CBS can help you get started with your cybersecurity assessment, reach out to our team today.