Choosing between a Security Information and Event Management (SIEM) solution and a Security Operations Centre (SOC) depends on your organisation’s security maturity, resources, and compliance needs.
For Australian SMBs and enterprises, outsourcing a managed SOC and SIEM service is often the most practical and cost-effective way to achieve enterprise-grade security without the high overhead of an in-house team.
Global cyber crime is expected to rise from $3 trillion (USD) in 2015 to a staggering $10.5 trillion by 2025. A string of large-scale data breaches across Australia demonstrates no company, large or small, is immune from online thieves. The full list of data breaches in 2022 is frightening, illustrating just how exposed organisations across Australia are and the need to make significant steps forward to protecting our data assets.
That’s why companies across every sector are tasked with hardening their cybersecurity defences by employing strategies such as Security Information and Event Management (SIEM) and establishing a Security Operations Centre (SOC). Without heightened monitoring, organisations are often left unaware that cybercriminals are orchestrating an attack until after the fact. By better understanding SIEM vs SOC, industry leaders can make informed decisions about how to invest in managed IT and cyber security.
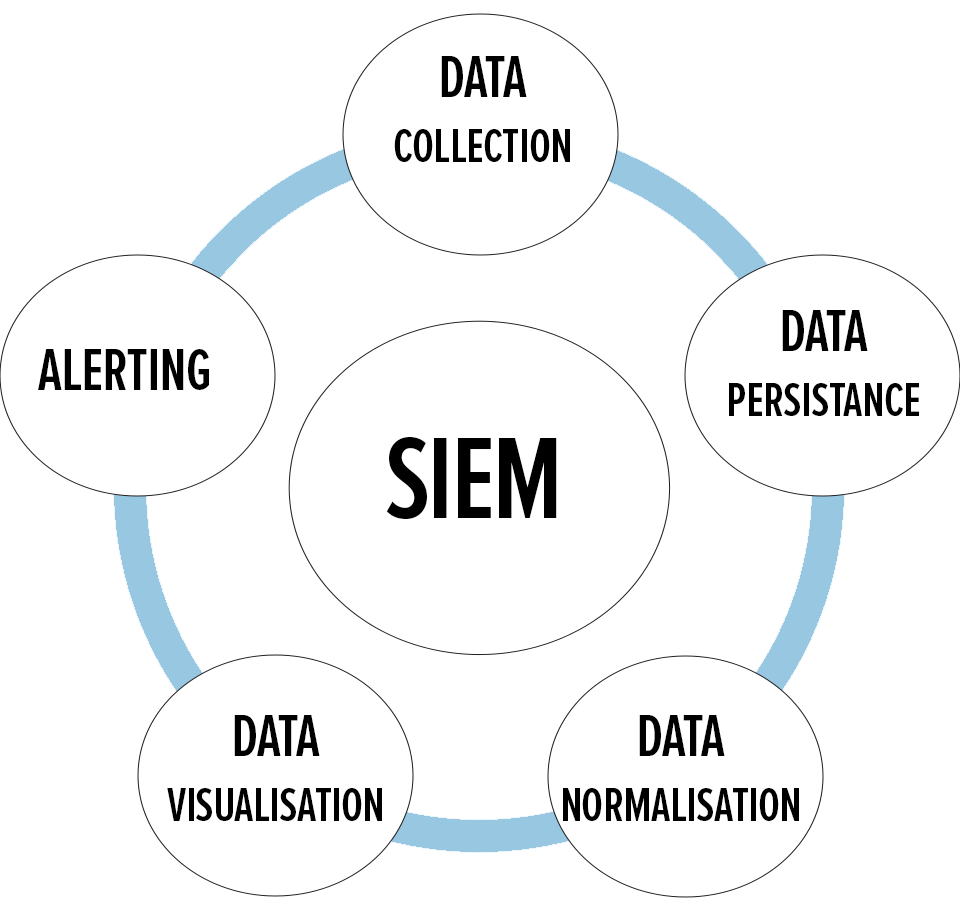
Cyber security professionals developed SIEM as a logical progression of two other approaches. The strategy blends facets of security information management (SIM) and security event management (SEM) into a holistic system of real-time network monitoring, analysis, and tracking. In the simplest of terms, SIEM helps improve vulnerability management and deter emerging threats before hackers can penetrate or disrupt a business network.
What makes SIEM uniquely effective are the methods used to identify potential threats. The cyber security practice focuses on anomalies within the user behaviour space. Using automation and artificial intelligence, it outpaces the log management approach of the past.
For example, SIEM nets event data across an operation’s complex network. Events and logs from end-user devices, servers, firewalls, and security appliances, are collected and automatically scrutinised. This provides IT security teams the ability to identify and investigate security alerts and incidents. It also presents a forward-thinking way to handle compliance and governance.
Few cybersecurity insiders would disagree that SIEM solutions deliver enhanced protection, as well as other benefits. The ability to respond to a cyber attack in real time can mean the difference between insulating intellectual property and sensitive client data from hackers or having it sold on the dark web. That being said, if SIEM practices were easy to implement, every business would already have them in place. These are challenges associated with SIEM.
Today’s corporate networks have a wide array of cybersecurity components. These typically include enterprise-level firewalls, intrusion detection, routers, antivirus software, and malware protection, among others. Bringing the alerts generated by these safety measures under one roof requires a sophisticated understanding of SIEM. Considerable fine-tuning will be needed to maximise the effectiveness of SIEM solutions and that means working with an experienced managed IT and cyber security firm.
Existing business networks are not a blank slate. The vast majority of them have cyber security measures in place that are somewhat outdated, given the advancing efforts by cybercriminals. The initial challenge of implementing a next-generation SIEM solution calls for integrating current cyber security protocols. The need to modernise an organisations network is key to establishing an agile and secure IT environment that can support modern work as well as business demand. Upgrading your network could be a key consideration when implementing an effective SIEM.
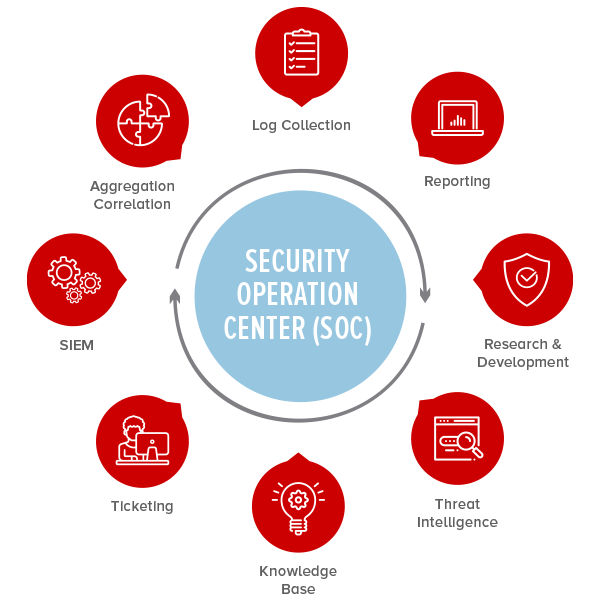
A Security Operations Center (SOC) is the hub of an organisation's security infrastructure and serves as a centralised source of monitoring, detecting and responding to cybersecurity threats. Staffed by a dedicated team of cyber security professionals, they use leading edge software, systems and tools to centralise the monitoring and analysis of cyber threats, and how to respond. The SOC location can be within a business facility or run remotely by a third-party firm. The key to such cyber security centres is staffing them with experienced professionals who possess niche expertise.
SOCs are staffed with IT professionals who use advanced technology solutions such as Artificial Intelligence (AI), Machine Learning (ML), analytics, correlation and automation to detect, investigate and respond both to internal alerts generated by an organisation’s security systems and external intelligence sources. SOCs work constantly to proactively monitor all of the organisation’s networks for indicators of compromise or malicious activity that might endanger the company’s data or reputation. After identifying a potential threat, SOC teams coordinate with other departments within the organisation to develop proper containment strategies in order to protect data from unauthorised access or disruption. SOCs also monitor news outlets for information about new threats so that they can act quickly if necessary. Ultimately, SOCs help organisations efficiently manage cyber risk by quickly detecting and eliminating cyber threats before they turn into costly attacks.
It’s important to keep in mind that every cyber security method comes with inherent strengths and weaknesses. The manner in which the challenges are addressed generally determines whether the approach achieves its goals. Although a SOC typically has two areas of adversity, they can be overcome by enlisting the support of experienced cyber security experts.
Hackers continue to flood employee emails with phishing schemes and level network surface attacks at an increasingly high rate. Whenever a genuine or potential threat emerges, the SOC team fields an alert. To put that in context, consider the number of times your personal devices warn you about a suspicious website or message. Multiply that by every employee working on the internet and the number of malware-laced emails attempting to reach inboxes.
The ability to staff an in-house SOC team has become something of a non-starter for many companies. A persistent shortage of cyber security professionals exists and maintaining 24/7 staffing would come at a debilitating cost. Outsourcing a SOC, as well as overall cybersecurity, has become the most cost-effective way to protect digital assets. For many organisations, in terms of establishing a SOC, outsourcing may be the only practical way to implement.
Transform Your Cyber Defense: Prioritised Actions for Staying Ahead of Threats.
DownloadThe idea of an SOC vs SIEM dichotomy misses the mark. SIEM SOC services are more complementary than a type of either-or approach. The SOC is a team of professionals who are dedicated to taking proactive measures to avert data breaches. A SOC team will utilise a SIEM as part of their role. The SIEM tools brought into play help them monitor, assess, and decide how to address threats. Employing SOC services utilising an effective SIEM ranks among the best ways to create a superior cyber security uplift.
While SOC and SIEM deliver excellent cyber security benefits, utilising both practices only amplifies them. On the one hand, SIEM can greatly improve a business’s ability to identify threats before hackers infiltrate a network. With this information, proactive SOC team members can respond and expel cyber security risks.
Although a veritable laundry list of SIEM SOC services benefits could be compiled, there’s a more fundamental way of understanding the advantage. Adopting a proactive vs a reactive strategy to your cyber defence puts organisations on the front foot. It means threats are detected faster, driving an almost immediate response and avoid dwell time that puts an organisations information assets at risk.
Industry leaders outside the managed IT security sector would be well served to enlist the support of a third-party provider. Cyber security professionals typically undertake a cyber security assessment before recommending the best solutions. This may involve a thorough analysis and targeted approaches such as penetration testing, among others, for identifying strengths and vulnerabilities.
The outcome of a cybersecurity review is then balanced against pragmatic considerations such as threat risk and cost. The best way to know which cyber security solution makes the most sense is to enlist the services of an experienced Managed Security Services Provider (MSSP).
The high cost of hiring cyber security professionals has made outsourcing business friendly. Companies save money on employee salaries while receiving the expertise from teams of people they might otherwise not be able to hire who can also leverage lessons learnt from a variety of customers. The decision to work with a partner that has a team of cyber security professionals remains the most practical way to maintain robust defences. These are the benefits associated with outsourcing SIEM SOC services.
Organisations that elect to outsource managed SIEM benefit from configuration meeting best practice while also being expertly tailored to meet your needs. They also enjoy improved threat recognition and vulnerability management.
Outsourcing a SOC makes the ability to respond to threats in real time, 24/7/365, cost effective. It also maximises the ability of companies to take proactive measures to deter hackers from disrupting their day-to-day operations.
In effect SOC requires SIEM to be implemented, as such embracing third-party SOC and SIEM services amplifies the benefits of both approaches.
When choosing an MSSP to handle SOC and SIEM services, take your time and thoroughly vet the firm. The managed IT security outfit must possess the expertise, experience, and team members to roll out the cyber security practices. Once in place, an MSSP must also have the staff members to maintain 24/7 oversight.
Canon Business Services provides scalable and effectively managed IT security for organisations across industries. If your company would benefit from the expertise of a fully staffed MSSP, contact CBS for personalised support.
To help you get started or continue on your cyber security journey, our team would initially start with a Cybersecurity assessment to establish a baseline and determine the best strategy moving forward, that combines quick wins along with establishing longer term cyber defences.
CBS is one of Australia’s most highly accredited Cybersecurity services organisations. We’re proud to be among the few Australian MSSPs in the Microsoft Intelligent Security Association (MISA), which means we can better defend you against a world of increasing cyber threats. CBS is one of the few MSSP’s holding three Azure Advanced Security Specialisations, across Identity & Access Management, Cloud Security and Threat Protection. We know whats required to safeguard your organisation today.
Understanding the differences between SIEM and SOC solutions is crucial for developing a robust cybersecurity strategy. SIEM provides the tools for real-time monitoring and analysis, while SOC offers the human expertise to respond to threats effectively. Together, they form a complementary defense mechanism that enhances an organisation's ability to protect its data assets. For businesses in Australia, partnering with an experienced Managed Security Services Provider (MSSP) like Canon Business Services can ensure that both SIEM and SOC solutions are implemented and managed effectively, providing comprehensive security coverage and peace of mind in the face of evolving cyber threats.